about.exe - part 2
Unfortunately the malware from part 1 can't pull down the stage 2 components because the botnet server it was pointing to is offline. Thankfully, I already had copies of the stage 2 components. For the sake of completeness on this part I'll include a few other bits of information about the original traffic. Here's a shot of the encrypted POST request that this malware attempts to make:
You may recognize the /gate.php URI it's attempting to make the POST request to. This should be familiar to anyone who has worked with it before that this is similar to the way some Zeus variants work (Specifically, this looks a LOT like Pony PWS based on the /gate.php POST requests, seen here in my previous post: http://goo.gl/H3fi0 -- however, analysis of the dropped files and other behavior, seen later, proves that it is not actually Pony/Zeus at all). If the botnet server were online in this case, we would also see some GET requests for additional .exe files (in this case, there were originally two of them... 1.exe and 6.exe). Thankfully I have the two additional exe files from a previous analysis, but I don't have a capture of the original traffic to show you (sorry!).
I do know where the files came from, however:
Botnet IP: 85.195.91.179
Infected botnet domain: catch-cdn.com
URLQuery page: http://urlquery.net/report.php?id=3123478
Scroll back up and look at the TCP stream - notice the googleapis.com host? It's not actually hitting google, the Host parameter in the traffic is spoofed. Something to keep an eye out for! (PS: I see this a lot with various malware, it's not all that uncommon)
1.exe Analysis
The first exe that comes down is 1.exe. VT hits identify this as being part of the Trojan.Graftor family (but don't ever trust automation 100%). Here's some info on it:
File hash: 80E7EE258BCC1293664B687BC2378009
VT Info: https://www.virustotal.com/en/file/aead29b91cf98f141d1a2475e73f42450c7576524079a5788176b4074dc02968/analysis/
So - let's run this thing and see what it does. :)
The only immediately obvious thing is that it spawns a flash updater installer:
Further investigation reveals this to be fake (as if we didn't know that already). The 'download' will 'fail' when it reaches 100%. Here's the file info on it:
File hash: 2FF9B590342C62748885D459D082295F
VT Info: https://www.virustotal.com/en/file/672ec8dceafd429c1a09cfafbc4951968953e2081e0d97243040db16edb24429/analysis/
0/47 hits huh? The GET request is also going out to 96.17.130.70 which is part of the absolutely massive Akamai CDN. It's also where fpdownload.macromedia.com points to, which makes it look legit, but we already know it's easy to fake a hostname, and Akamai CDN isn't run by Adobe, which only furthers our suspicion of this being malicious. If you take a look at some of the related hash results on VT, they will confirm that this thing is definitely bad:
I'm not going to do anything else with the flash updater, since that's not really what we're focusing on here.
1.exe copies itself to the following directory before deleting the original:
This is the second file our original malware component from part 1 ends up downloading.VT Info: https://www.virustotal.com/en/file/aead29b91cf98f141d1a2475e73f42450c7576524079a5788176b4074dc02968/analysis/
So - let's run this thing and see what it does. :)
The only immediately obvious thing is that it spawns a flash updater installer:
File hash: 2FF9B590342C62748885D459D082295F
VT Info: https://www.virustotal.com/en/file/672ec8dceafd429c1a09cfafbc4951968953e2081e0d97243040db16edb24429/analysis/
0/47 hits huh? The GET request is also going out to 96.17.130.70 which is part of the absolutely massive Akamai CDN. It's also where fpdownload.macromedia.com points to, which makes it look legit, but we already know it's easy to fake a hostname, and Akamai CDN isn't run by Adobe, which only furthers our suspicion of this being malicious. If you take a look at some of the related hash results on VT, they will confirm that this thing is definitely bad:
- https://www.virustotal.com/en/file/045f08a99c4b4c39702460382853625211f1d515678179e961dfb31a9a381434/analysis/
- https://www.virustotal.com/en/file/32efef60bbf1b7ed2dad85eec0bb01da3ede48ff8853fb751ee4243304d2309f/analysis/
I'm not going to do anything else with the flash updater, since that's not really what we're focusing on here.
1.exe copies itself to the following directory before deleting the original:
- C:\$Recycle.Bin\S-1-5-21-2642609715-2370073529-3293857777-1000
A file named Msimg32.dll is created in the path above as well. Info below:
File hash: 4D7AD34C54577DDE3110405ACB28AB42
Seeing references to ZeroAccess in the VT results, but again - we can't always trust automation. However, we're headed in the right direction... more on that later. :)
Looking at the network traffic really starts putting the pieces of the puzzle together. We see many GET requests for the domain e-zeeinternet.com.
Domain: e-zeeinternet.com
IP: 209.68.32.176
URI regex: "\/count\.php\?page\=\d{6}\&style\=LED\_g\&nbdigits\=\d"
Sample URI: /count.php?page=953000&style=LED_g&nbdigits=9
You can see the GET requests here in Wireshark:
I've seen this sort of traffic before, but it didn't immediately come to me where I had seen it. With the help of @MalwareMustDie, we were able to figure out just where this came from, but it wasn't that traffic that gave it away.
Looking further into the pcap I saw this:
j.maxmind.com is a legitimate geolocation service, but it's a little unusual to see this sort of thing in any traffic where we didn't do this manually, right? A little digging leads us to some VT results for a few ZeroAccess samples (thanks again to @MalwareMustDie for helping me uncover this!). Take a look at "Behavioral Information" under "HTTP requests":
ZeroAccess VT Sample 1: https://www.virustotal.com/en/file/5692fc972b404a16f19c6005b84acdac346ffcf5d5c1d1a43078de6f23c17f6a/analysis/
And another:
ZeroAccess VT Sample 2: https://www.virustotal.com/en/file/8f4f8ca94f683b4afe4f1003935933805ee6b35ea5aaf096724a58d37860952a/analysis/
Okay, so we KNOW that ZeroAccess uses j.maxmind.com. My guess is that it's used by the botnet owner to identify the rough location of all the infected hosts.
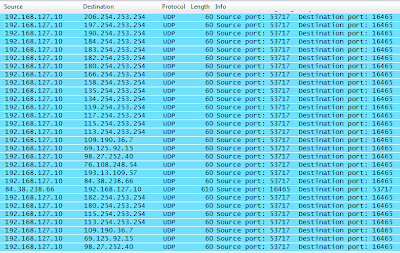
Okay, back to the pcap again and there's some really interesting looking UDP traffic:
LOTS of UDP requests to/from non-standard ports. Interesting. Let's dig a little deeper into this and see what we can find. First, let's point out some oddities here:
- Most of the UDP requests have a destination port of 16465
- The common pattern of destination IP's follows this format: xxx.254.253.254
This was the second part of the traffic that pointed solidly in the direction of this being part of ZeroAccess. Here's a GREAT analysis of ZeroAccess by @MalwareMustDie: http://malwaremustdie.blogspot.jp/2013/02/blackhole-of-closest-version-with.html
If you search for "UDP\16465", you'll see a lot of similarities. However, we know that Zeus also uses similar methods, so what else can we look into to identify this malware? In this case, the registry changes also help to support the suspicion that this is ZeroAccess.
Seeing lots of changes to \Internet Settings\ZoneMap - this is a strong indicator of ZeroAccess. In reading through the MMD article linked above, we can see that there are other registry indicators - specifically changes made to \System\CurrentControlSet\services\SharedAccess, seen here:
At this point, I think we can reasonably conclude that this is, in fact, ZeroAccess. Goes to show just how much we have to pay attention when doing malware analysis, or we may head off in the wrong direction. :)
So, in summary:
Malware Type: ZeroAccess Trojan
Initial downloader filename: about.exe (Analysis covered in Part 1 of this post)
First dropped file: 1.exe
1.exe hash: 80E7EE258BCC1293664B687BC2378009
Behavioral details:
- Spawns downloader for Adobe Flash Installer
- Copies itself to C:\$Recycle.Bin\S-1-5-21-2642609715-2370073529-3293857777-1000
- Creates file Msimg32.dll under recycle bin directory above
- File hash: 4D7AD34C54577DDE3110405ACB28AB42
- VT Info: https://www.virustotal.com/en/file/94941aebd9d43f5077053f6557301114d7014ea04a123369ae0c3f8950e8e247/analysis/
- Makes many changes under the following registry keys:
- \System\CurrentControlSet\Services\SharedAccess
- \Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zone Map
- Lots of UDP traffic bound for port 16465
- UDP/16465 traffic destinations:
- 206.254.253.254 (University of Texas, United States)
- 197.254.253.254 (Canar Telecomm, Sudan)
- 190.254.253.254 (Colombia Telecomm, Colombia)
- 184.254.253.254 (Sprint/Nextel, United States)
- 183.254.253.254 (China Mobile Communication Corporation, China)
- 182.254.253.254 (Tencent, China)
- 180.254.253.254 (Menara Multimedia, Indonesia)
- 166.254.253.254 (Service Provider Corporation, United States)
- 158.254.253.254 (Sprint, United States)
- 134.254.253.254 (DoD Network Information Center, United States)
- 119.254.253.254 (Langfang University, China)
- 117.254.253.254 (Bharat Sanchar Nigam Limited, Hong Kong)
- 115.254.253.254 (Reliance Communication, Ltd, India)
- 113.254.253.254 (Hutchinson Global Communication, China)
- 109.190.36.7 (OV Telecomm, France)
- 69.125.192.15 (Optimum Online, United States)
- 98.27.252.40 (Time Warner, United States)
- 76.108.245.54 (Comcast, United States)
- 193.13.109.57 (Swipenet, Sweden)
- 84.38.238.66 (Uniserver Internet B.V., Netherlands)
- Domains contacted (Note: domain names may be spoofed)
- j.maxmind.com (50.22.196.70, Maxmind, United States)
- e-zeeinternet.com (209.68.32.176, Pair Networks, United States)
- fpdownload.macromedia.com (96.17.130.70, Akamai Technologies, Inc, United States)
- catch-cdn.com (85.195.91.179, Xianbiao Xu Xianbiao, Denmark)
And that only covers the first dropped file (and the downloader).
On with the next file...
6.exe Analysis
File hash: F604DAF8E12EFAE8302F0ECC2BEDC5CA
VT Info: https://www.virustotal.com/en/file/010ef31d508c7338da2efb0128b518d290b7eaa8ae4345db2999abdf67a31acf/analysis/
It comes from the same location as 1.exe above:
Botnet IP: 85.195.91.179
Infected botnet domain: catch-cdn.com
URLQuery page: http://urlquery.net/report.php?id=3123478
Ok, so what does it do?
Nothing immediately obvious, but poking around shows us that it does quite a bit (and it doesn't take long before it really goes crazy... more below). First, it creates two files at the following location:
File hash: F604DAF8E12EFAE8302F0ECC2BEDC5CA
VT Info: https://www.virustotal.com/en/file/010ef31d508c7338da2efb0128b518d290b7eaa8ae4345db2999abdf67a31acf/analysis/
Filename: B6EF0443E25512750000B6EE4D5C18F9.ico
File hash: Unknown (see below)
VT Info: N/A
As I was trying to gather more information about the files above, the malware just hijacked everything on my VM with this...
Ok, so what does it do?
Nothing immediately obvious, but poking around shows us that it does quite a bit (and it doesn't take long before it really goes crazy... more below). First, it creates two files at the following location:
- C:\ProgramData\B6EF0443E25512750000B6EE4D5C18F9\
File hash: F604DAF8E12EFAE8302F0ECC2BEDC5CA
VT Info: https://www.virustotal.com/en/file/010ef31d508c7338da2efb0128b518d290b7eaa8ae4345db2999abdf67a31acf/analysis/
Filename: B6EF0443E25512750000B6EE4D5C18F9.ico
File hash: Unknown (see below)
VT Info: N/A
As I was trying to gather more information about the files above, the malware just hijacked everything on my VM with this...
Followed by this:
I figured it just hid the desktop, since everything quit working the way I wanted it to work. I thought, "I know! I'll just run Sysinternals Desktops and get control of my stuff back!"... And then... DENIED:
Really? *sigh* A little more poking around lead me to quickly discover that this happened with EVERY program I tried to launch. Out of curiosity, I clicked on one of the links in the fakeAV program to see what it would do. It launched a fake web browser and tried to reach out to this:
- hxxp://109.206.174.48/payform2/?&lid=3070033&affid=03600&nid=B6E71275&group=sca
This rabbit hole just keeps going and going... so, I will break the remaining analysis of 6.exe into part 3, which I will try to have up around the same time next week. As always, stay tuned!
-SM










No comments:
Post a Comment